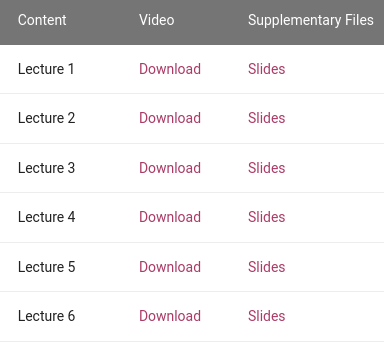
Dr. Fabian Yamaguchi
Computer Scientist, Lecturer, Hacker.
Hi, I am a computer security professional, software engineer, and professor based in Cape Town, South Africa. Reach out for vulnerability assessments, talks, and courses on vulnerability discovery and exploitation.
What's new?